In some walks of life, cybersecurity is considered a tax or an expense rather than an enabler. Looking at cybersecurity as a tax is similar to concluding that locks on doors or a credit card verification device is also a tax. A tax is something people feel they pay and get little in return, this is not always the case but you get the idea.
Cybersecurity is a keystone of doing business on the Internet. It is as important as the quality of your web application; how the user interacts with your product or service and encourages clients to use your service if they can be assured there is a decent level of security surrounding their data and transactions.
As a security practitioner or a technologist, we may encounter cynics questioning the value of cybersecurity or you may have to justify why investment needs to be made into cybersecurity in order to keep the organization on a strong footing. The following are ways to demonstrate value.
Why are we doing cyber?
Measure, measure, measure…
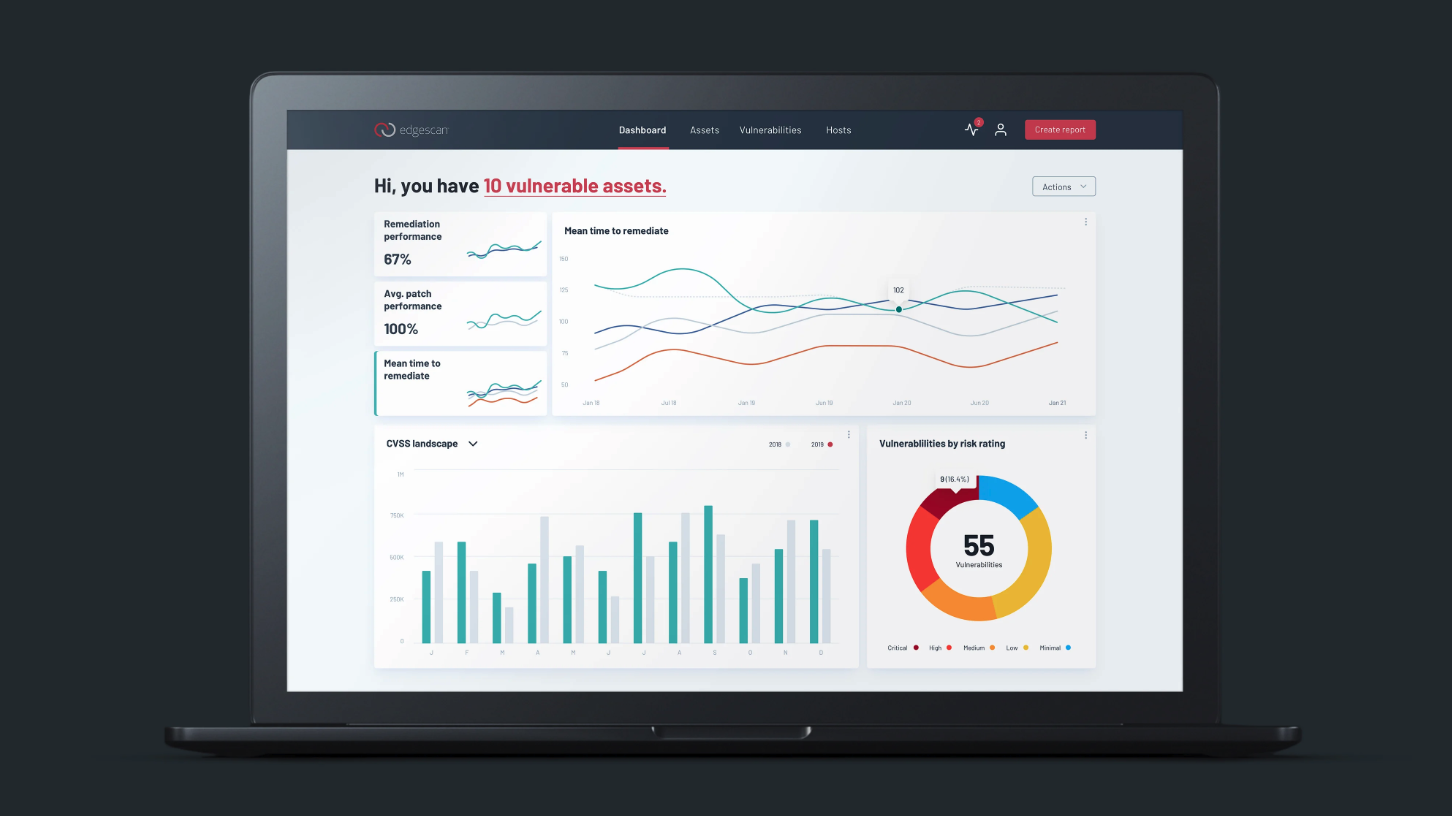
Consider metrics but in terms of explaining to the business let’s focus on some easily understandable ones such as:
Discovered Vulnerabilities (Internal and public facing)
- How many vulnerabilities are we discovering across the business as a whole?
- Which Business units / Locations appear to be more vulnerable?
- What is the average Risk (Risk Density) of discovered vulnerabilities?
- Which critical services are subject to vulnerabilities?
Speed of Remediation & Patching
- How quickly are we fixing Critical and High Risk vulnerabilities.?
- How quickly are we patching and how often do we audit for non-patched systems?
Location of Vulnerabilities
- What is the percentage of public facing vulnerabilities vs Internal/Non-public vulnerabilities?
- What is the risk profile of vulnerabilities based on location or exposure of the system?
Source of Vulnerabilities
- How many vulnerabilities are patch related?
- How many vulnerabilities are application/developer related?
- How many vulnerabilities are related to outsourced or B2B systems?
Potential Compliance Violations
- How many vulnerabilities violate compliance or quality standards (PCI/CIS/ISO etc)?
- What is the business impact of non-compliance based on the discovered vulnerabilities?
Detected Intrusion Attempts
- How many intrusion attempts are being observed for a given time period?
- What is the source of the intrusion attempts (Internal/External).
- What type of intrusion attempts are being observed?
- Is the intrusion against a service with known vulnerabilities?
Peer relativity
- How is the organization fairing compared to peer or global average in terms of mean time to remediate (MTTR), Risk density, Patching speed?
Vulnerability Discovery Cadence, System Deployment & Continuous Monitoring
- Tracking how often vulnerability assessment is occurring and which systems are in scope.
- How many systems are exposed to the public internet and what services are on the endpoints?
- How many new systems were deployed in the last period and what do they do?
These metrics can sometimes be difficult to track and nurture which is a challenge. Leveraging a risk dashboard covering both network / host and application layer risk metrics which is something worth considering. There is a trend towards integration of related systems to achieve this and something Edgescan has been dedicated to achieving for the past 5 years. Edgescan provides unparalleled vulnerability assessment and penetration testing monitoring, coupled with real-time continuous asset & API discovery for some of the worlds largest organizations.






