Penetration Testing as a Service has evolved beyond “a pentest in a portal.” Leading PTaaS platforms now combine continuous assessment, human-led depth, and intelligent prioritization so security teams can address real risk efficiently.
But not all PTaaS providers deliver the same capabilities. The market has fragmented between product-first vendors, retrofitting penetration testing quality and services-first organizations building platforms from years of security consulting experience.
Here’s what sets effective PTaaS apart – and why Edgescan’s approach aligns with what security analysts and enterprise buyers actually need.
The Market Context: What Gartner and Forrester Signal
Continuous Threat Exposure Management (CTEM) provides the strategic framework for modern security testing. Gartner’s 2024 research quantifies the impact: organizations that prioritize security investments through CTEM programs will realize a two-thirds reduction in breaches by 2026.
Forrester’s research emphasizes that proactive security depends on continuous testing and attack surface visibility, not point-in-time exercises. Both analyst firms highlight visibility, prioritization, and remediation as core outcomes.
The implication is clear: PTaaS providers that couple human-led depth with always-on assessment and strong prioritization capabilities align best with these analyst-validated outcomes.
What Makes Edgescan PTaaS Different
Unlimited DAST Built Into PTaaS
Edgescan’s PTaaS license includes unlimited automated vulnerability assessments (DAST) for covered assets, not as an add-on. Teams can run dynamic tests as often as needed, including authenticated flows, while reserving human testers for deeper scenarios.
This removes scan rationing and closes exposure windows between scheduled tests. Modern release cadence demands continuous assessment, not quarterly checkpoints.
Full-Stack Assessment in One Platform
Edgescan delivers unified assessment across web applications, APIs, networks, hosts, and mobile. This matters because exploitable attack chains often cross asset types – an API vulnerability combined with application weaknesses and host-level exposure creates the path attackers actually use.
Network Vulnerability Management operates as a first-class capability alongside application and API security. Attack Surface Management enhances discovery and scoping – the CTEM phase both Gartner and Forrester call essential for proactive programs.
Near False-Positive-Free Results Through Human Validation
All automated findings undergo expert validation before reaching your remediation queue. This human review layer reduces noise and saves engineering time chasing phantom issues.
According to Edgescan’s 2025 Vulnerability Statistics Report, 92% of vulnerabilities are validated through automated analysis, with the remaining 8% requiring human expert review. This hybrid approach eliminates false positives while maintaining assessment speed.
False positives represent the hidden cost center of application security and vulnerability management. Pre-validated findings accelerate mean time to remediation and preserve trust between security and engineering teams.
Certified Experts and Business Logic Testing
Edgescan’s delivery team includes CREST and OSCP-certified practitioners who perform deep manual testing. Critically, the PTaaS approach emphasizes authorization and business logic flaws – weaknesses that scanners routinely miss.
Business logic vulnerabilities exploit intended application functionality rather than code errors. They often represent the highest business risk but remain invisible to automated tools. Edgescan’s reporting shows a notable share of critical issues arising from business logic testing, underscoring its practical value.
A Penetration Testing Company With a Product
Edgescan’s PTaaS model grew from years of consulting delivery, then matured into a productized platform. This represents a fundamentally different approach than product vendors retrofitting penetration testing quality later.
The services-first foundation shows up in the workflow: unlimited retests, validated findings, and expert guidance embedded from the start rather than bolted on as premium add-ons.
Platform Breadth: PTaaS + DAST + NVM + ASM
Edgescan bundles PTaaS with DAST, Network Vulnerability Management, and Attack Surface Management for continuous discovery, assessment, and validation. This breadth reduces tool sprawl and helps correlate exposures across technology layers.
Prioritization That Reflects Actual Threat
Most security teams cannot remediate everything. Effective prioritization becomes essential. Edgescan’s AI Insights correlate each validated vulnerability with external threat signals and decision frameworks:
EPSS (Exploit Prediction Scoring System): Probability a CVE will be exploited in the near term, based on machine learning models from FIRST.
NIST LEV (Likely Exploited Vulnerabilities): A new metric estimating whether a CVE has already been exploited, complementing EPSS and KEV data.
SSVC (Stakeholder-Specific Vulnerability Categorization): A decision model for determining what to do next – defer, track, or act.
CISA KEV: Authoritative catalogue of vulnerabilities known to be exploited in the wild.
The platform automatically correlates vulnerabilities with these frameworks, producing context-aware prioritization in the UI and via API. Combining probability (EPSS), evidence of exploitation (LEV/KEV), decision policy (SSVC), and validated exploitability from testing ensures limited engineering time addresses the most consequential risk first.
How Edgescan Executes PTaaS in Practice
Scope and Discover: Attack Surface Management enumerates internet-facing assets, APIs, and hosts. Inventory stays current as environments change.
Continuous Assessment: Unlimited DAST and Network Vulnerability Management surface candidate issues continuously.
Human Validation and Deep Testing: Certified analysts triage, validate, and probe business logic, authentication and authorization flows, and complex API paths.
Prioritize with AI and Threat Intelligence: EPSS, LEV, SSVC, and KEV mapping augments validated findings to create ranked remediation backlogs.
Remediate and Retest: Unlimited retests and expert guidance close the loop quickly, keeping status accurate for auditors and leadership dashboards.
Why This Approach Matters to Buyers
Analyst-Aligned Outcomes: Continuous testing combined with ASM visibility, validation, and prioritized remediation aligns precisely with Gartner’s CTEM model and Forrester’s proactive security guidance.
Lower Total Cost to Fix: Teams waste less time on false positives and fewer cycles coordinating separate tools for discovery, scanning, testing, and prioritization. Validated findings, unlimited DAST, and unlimited retests address this friction directly.
Depth Where It Counts: Certified practitioners focusing on business logic and authenticated states uncover risk classes unattainable with scanners alone. Yet the workflow still operates like a product, not a series of emails and PDF reports.
The Evidence of Full-Stack Value
Web, API, and network vulnerabilities don’t exist in isolation. Attackers chain weaknesses across technology tiers. Unified testing across these layers prevents cross-layer blind spots.
The API security challenge exemplifies this need. According to Edgescan’s data, API-related vulnerabilities account for significant portions of critical security findings. Organizations handling API-dependent architectures need testing that understands these attack patterns.
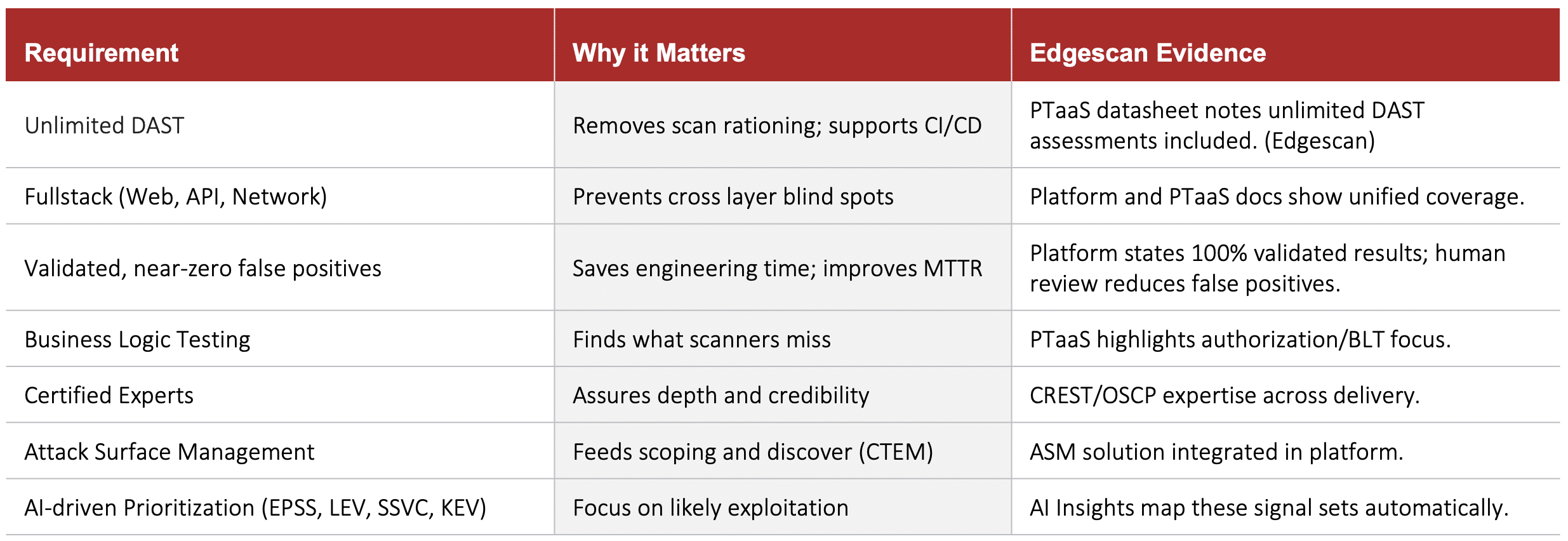
Buyer’s Checklist: Key Capabilities
When evaluating PTaaS providers, consider these requirements:
Buyer’s checklist (and how Edgescan maps)
Unlimited DAST: Removes scan rationing and supports continuous integration and deployment workflows.
Full-Stack Coverage: Prevents cross-layer blind spots across web, API, and network infrastructure.
Validated Results: Saves engineering time and improves mean time to remediation by eliminating false positives.
Business Logic Testing: Finds what scanners miss – the high-risk vulnerabilities exploiting intended functionality.
Certified Experts: Ensures depth and credibility in manual testing activities.
Attack Surface Management: Feeds scoping and discovery as part of continuous threat exposure management.
AI-Driven Prioritization: Maps EPSS, LEV, SSVC, and KEV automatically to focus remediation on likely exploitation.
Moving Forward
Effective PTaaS blends the continuous reach of unlimited DAST, the depth of certified human testing including business logic analysis, and the breadth of ASM and network assessment. All of this gets prioritized through AI-mapped threat intelligence using EPSS, NIST LEV, SSVC, and CISA KEV.
The operational outcome matters most: validated, near false-positive-free findings translate to faster risk reduction and measurable cost savings. This aligns with Gartner’s CTEM guidance and Forrester’s emphasis on proactive security through continuous testing.
Organizations serious about vulnerability management need platforms built from security expertise first, not products with consulting services retrofitted later. The difference shows up in validated results, unlimited retesting, business logic coverage, and intelligent prioritization that reflects how attackers actually operate.
Ready to evaluate PTaaS that delivers on these capabilities? Start here.