
Unified. Continuous. Accurate.
Welcome to Edgescan, the leading platform for continuous security testing, exposure management, and Penetration Testing as a Service (PTaaS). Gain comprehensive visibility into your cyber footprint with our advanced solutions, designed to provide Continuous Threat and Exposure Management (CTEM). From initial discovery to prioritization and remediation, Edgescan ensures your organization’s security is robust and proactive.
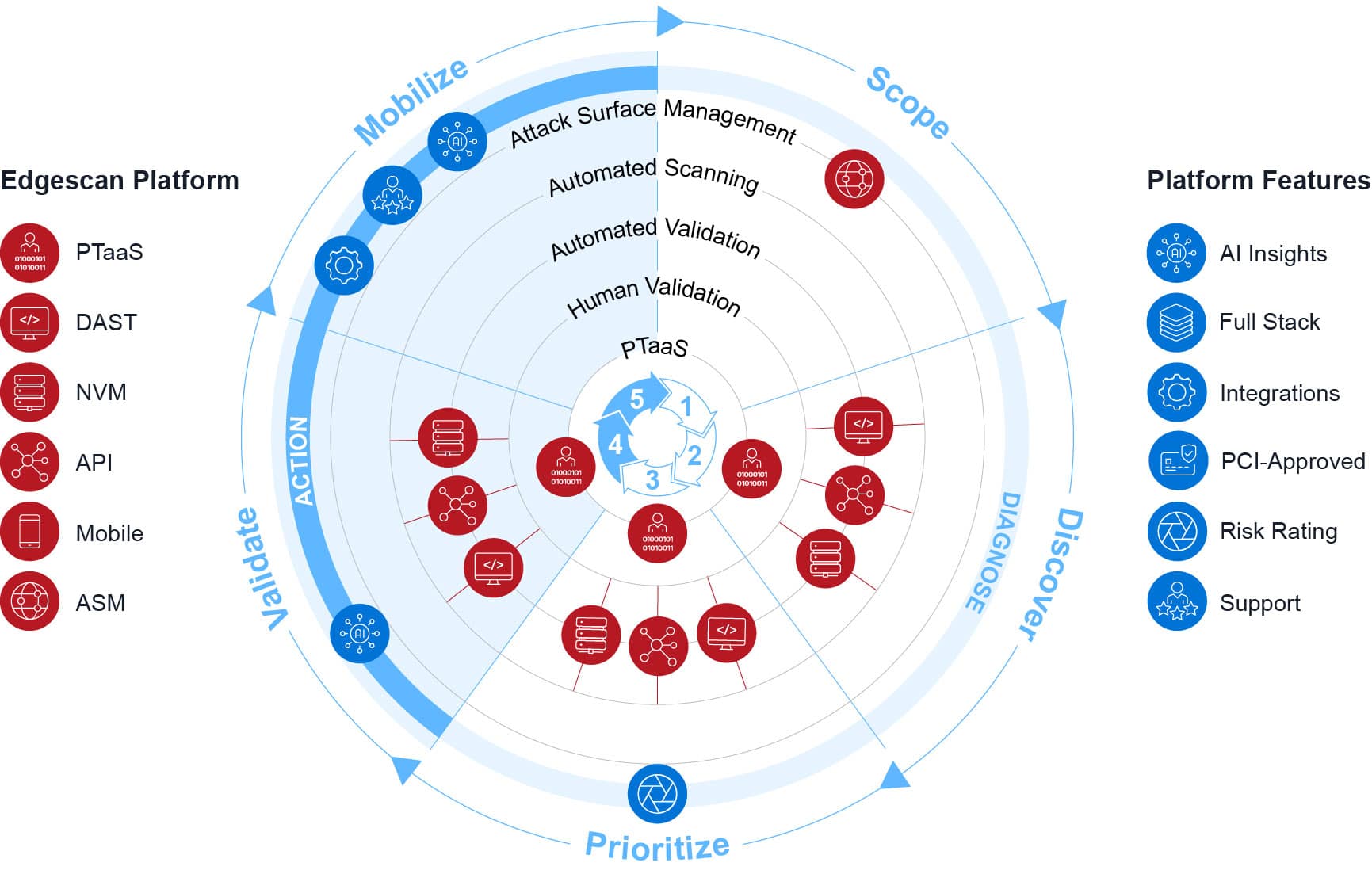
Exposure management
Edgescan’s exposure management solution enhances traditional vulnerability management by prioritizing remediation based on real risk levels. This approach ensures security teams focus on the most critical threats first, reducing overall exposure and improving response times.
Utilize systems like EPSS, CISA KEV, and CVSS, alongside Edgescan’s proprietary EVSS, to prioritize vulnerabilities.
Only real and actionable results are delivered, eliminating false positives.
Schedule assessments anytime and retest on demand, ensuring ongoing accuracy.
Key features
Comprehensive
asset discovery
and assessment
Utilize Attack Surface Management (ASM) to identify assets requiring protection.
Perform vulnerability assessments with a blend of automated scanning and human expertise, ensuring 100% validated results.
Prioritize and remediate vulnerabilities quickly with actionable intelligence.
Best-in-class testing across all platforms
Conduct thorough testing across networks, APIs, web applications, and mobile applications.
Use validated vulnerability intelligence and traditional scoring systems for compliance.
Leverage proprietary risk and breach rating systems to focus on the most critical vulnerabilities.
Hybrid Approach and continuous testing
Combine automated continuous testing with expert validation for near 100% accuracy.
Access consultancy-grade penetration testing delivered by certified security experts (CREST, OSCP).
Enjoy unlimited retesting and exposure management across all infrastructure.
Advanced AI experts
Utilize Edgescan AI Insights to analyze vulnerability data in real-time.
Benefit from strategic activities related to ransomware prevention, compliance, training, and anomaly detection.
Proprietary data lake for vulnerability intelligence
Store all vulnerability data in our growing proprietary data lake, shared across solutions.
Our proprietary data lake is used to preserve accuracy using intelligent data science and analytics.
Comprehensive
asset discovery
and assessment
Utilize Attack Surface Management (ASM) to identify assets requiring protection.
Perform vulnerability assessments with a blend of automated scanning and human expertise, ensuring 100% validated results.
Prioritize and remediate vulnerabilities quickly with actionable intelligence.
Best-in-class testing across all platforms
Conduct thorough testing across networks, APIs, web applications, and mobile applications.
Use validated vulnerability intelligence and traditional scoring systems for compliance.
Leverage proprietary risk and breach rating systems to focus on the most critical vulnerabilities.
Advanced AI experts
Utilize Edgescan AI Insights to analyze vulnerability data in real-time.
Benefit from strategic activities related to ransomware prevention, compliance, training, and anomaly detection.
Hybrid Approach and continuous testing
Combine automated continuous testing with expert validation for near 100% accuracy.
Access consultancy-grade penetration testing delivered by certified security experts (CREST, OSCP).
Enjoy unlimited retesting and exposure management across all infrastructure.
Proprietary data lake for vulnerability intelligence
Store all vulnerability data in our growing proprietary data lake, shared across solutions.
Our proprietary data lake is used to preserve accuracy using intelligent data science and analytics.
Contact us for more information on how Edgescan can help secure your business.
Full stack coverage: web applications, network layer (host/server) and APIs
Web applications (authenticated and unauthenticated), API’s (JSON, XML, WSDL, YAML and Graph), microservice architecture, single page applications, mobile applications.
Covering cloud endpoints, public and non public systems, Edgescan delivers continuous vulnerability detection and exposure management.
Why choose Edgescan?
Edgescan’s exposure management solution enhances traditional vulnerability management by prioritizing remediation based on real risk levels. This approach ensures security teams focus on the most critical threats first, reducing overall exposure and improving response times.
Accuracy and depth
Human expertise
Scalability
From small businesses to global enterprises, Edgescan scales to meet your needs.
Proven exploits
Focus only on what is proven to be an active threat and proven to be real.
Proactive security
Stay ahead of threats with continuous monitoring and rapid remediation.
Accuracy and depth
Human expertise
Scalability
From small businesses to global enterprises, Edgescan scales to meet your needs.
Proven exploits
Focus only on what is proven to be an active threat and proven to be real.
Proactive security
Stay ahead of threats with continuous monitoring and rapid remediation.
IT MANAGER
IT SECURITY MANAGER
NETWORK ADMINISTRATOR
CYBERSECURITY ANALYST
IT MANAGER
SECURITY OPERATIONS LEAD
CHIEF INFORMATION SECURITY OFFICER
Latest Blog Posts
As cloud-native infrastructure becomes the standard for modern enterprises, the demand for scalable, integrated security solutions has never been greater. …
Enterprises deploy code weekly. Some push changes daily. But traditional penetration testing still operates on quarterly schedules, creating dangerous security …
Security teams face an impossible challenge. Thousands of vulnerabilities flood their dashboards daily. Most will never be exploited. But buried …





