Learn why an effective pen testing solution must be a hybrid approach that leverages human intellect, advanced analytics and hard-core automation to effectively manage risk and cyber exposures.
Minimizing an organization’s attack surface is an ever-evolving, continuous challenge for security professionals. Testing and securing any, and all, assets facing the public internet, including public clouds, private clouds, data centers and more, can be a daunting and never-ending task. An effective strategy must include penetration testing, vulnerability management, and attack surface management tools at a minimum, combined with a thorough incident response and remediation process. Without any one of these key components – the strategy is “weak,” to say the least. Let’s look at the first component of this strategy: penetration testing.
What is Penetration Testing?
Penetration testing or “pentesting” is an established security best practice to find exploitable vulnerabilities and unintentional data exposure within an enterprise infrastructure. While a myriad of pen testing tools from various vendors provides this capability, the technology and its use have evolved significantly in recent years. Now security teams should consider Penetration Testing as a Service (PTaaS) to deliver these essential security measures.
So, what exactly is PTAAS?
PTAAS helps organizations better manage security risks, mitigate data breaches, and increase safe business continuity by leveraging a hybrid model that utilizes human intellect coupled with automation and analytics. Delivered as a service to offer greater scale, agility, and risk awareness, this type of assessment is essential for maintaining compliance with industry regulations and security frameworks within hybrid environments.
Edgescan’s PTaaS solution does just that. It combines proprietary penetration testing tools, risk-rated vulnerability data, and human intervention, so that enterprises can adopt PTaaS to harden their attack surface regardless of the size or configuration of their multi-cloud or hybrid environment.
PTAAS is nothing new, as a matter-of-fact Edgescan has been providing this service since 2016… and it is a fundamental solution of our platform.
How does PTAAS Work?
Effective PTaaS are a hybrid solution that combines the automation with human assessment, while integrated with advanced vulnerability management and analytics. PTaaS can be used for web application security, APIs, cloud assets, and network devices utilizing risk rating methodologies to prioritize remediation.
Edgescan Penetration Testing as a Service
PTaaS is a key component of our Edgescan Platform and is based on over seven years of technology and service evolution. The platform employs several risk scoring systems (i.e., CVSS, CISA KEV, EPSS) and our own Edgescan Validated Security Score (EVSS) to risk-rate results, with the goal of identifying and correcting any vulnerability – unknown, known, exploitable or otherwise.
The Edgescan PTaaS solution utilizes our security team’s extensive technical expertise as well as the entire suite of applications within the Edgescan platform to provide vulnerability assessment, exposure validation, and risk ratings. Our security experts offer battle-hardened security experience combined with countless industry accreditations such as CREST, OSCP, and CEH, to provide clients with deep wisdom and insight to readily resolve their security needs.
Edgescan is focused on testing sensitive areas of an asset and testing for vulnerabilities that cannot be uncovered through traditional vulnerability scanning alone. This hybrid penetration testing process of automation and combined human intelligence is what differentiates us from automated testing tools, scanning tools, and legacy services providing real and actionable results. Retesting of vulnerabilities is included to help ensure fixes are robust and resilient.
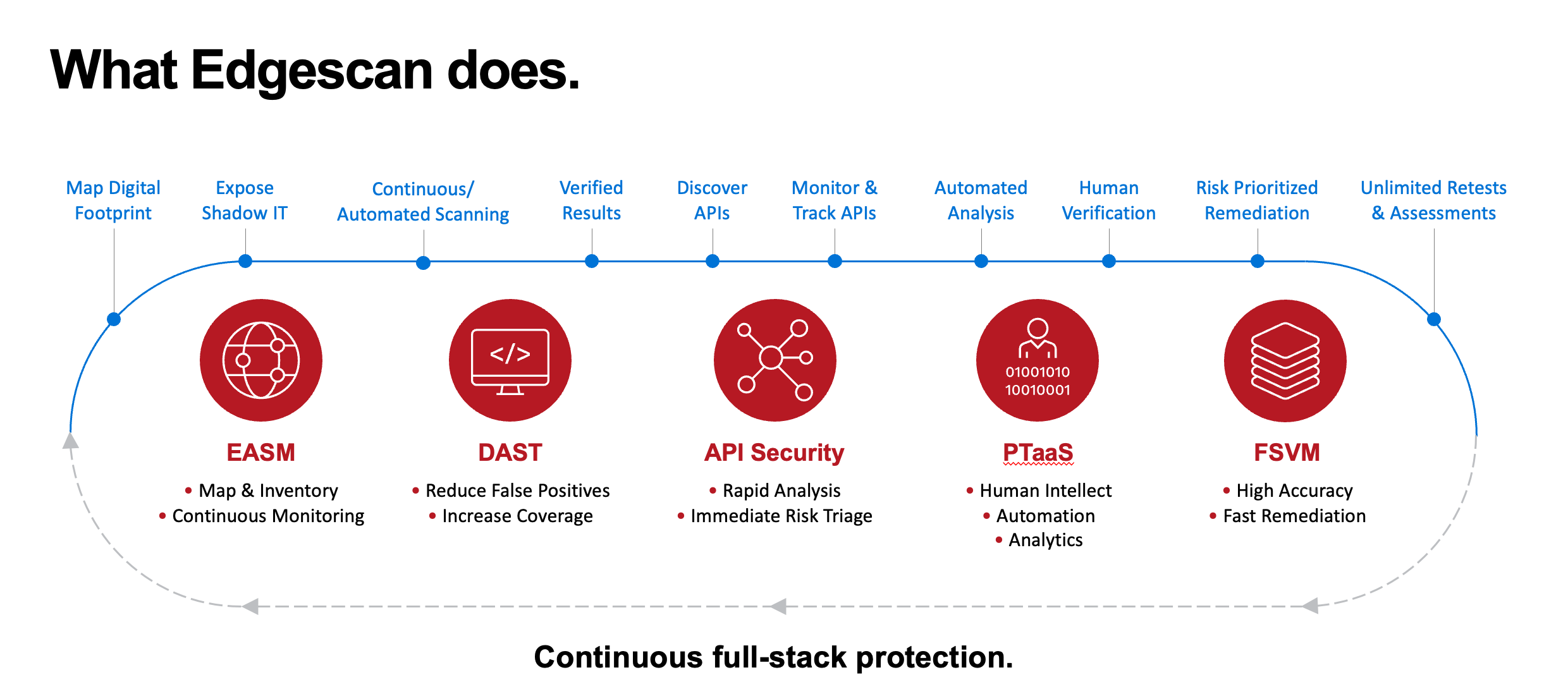
Extending Beyond PTaaS with Vulnerability Management and EASM
A Unique Multi-Layered Approach that Differentiates Edgescan from Tools and Stand Alone Solutions
As I referenced earlier, a major advantage that Edgescan offers customers is that PTaaS is integrated into the overall Edgescan platform that includes five essential security technologies, including Risk-based Vulnerability Management (RBVM), External Attack Surface Management (EASM), as well as Web application, and API Testing. All of these technologies use a common extensive data lake and an intuitive user interface, advancing vulnerability intelligence and simplifying operations and training. The “full stack” intelligence we garner by the combination of these tools is unparalleled in the industry and helps our customers manage their security posture.
Competitive solutions offer the above capabilities in a piecemeal, disparate fashion that only makes VM more difficult and error prone for their customers.
So, I recommend the Edgescan multi-layered approach with integrated pentesting and vulnerability management:
- EASM – What is exposed? What can be potentially hacked?
First, accurately detect and assess your entire attack surface, including cloud services, hosts, network devices, web apps APIs and more. - VM – What weaknesses do we have?
Then continuously monitor and detect all vulnerabilities and exposures across the full stack with high accuracy (Validation is King). Rank them by business concerns and tightly integrate with support operations to ensure timely remediation on what matters most. - PTaaS – How would a skilled attacker can do to penetrate your environment?
Now that your security team is armed with EASM and VM intelligence, perform laser-focused resilience tests on 1) areas of concern; 2) complex areas not suitable for automated testing (e.g., business logic) to determine the validity of any potential issues.








