Attack Surface Management (ASM)
Complete visibility. Unified view.
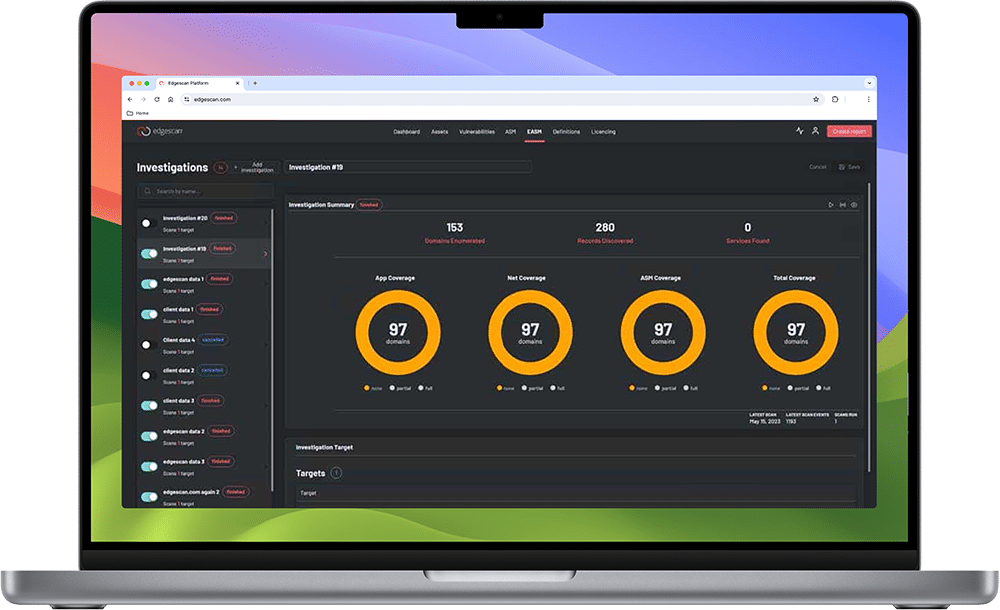
Edgescan ASM provides immediate asset discovery and visibility of an enterprise’s internet-facing estate, then continuously monitors the attack surface as it evolves and changes.
In today’s multi-cloud world, enterprises require an external attack surface management solution that effectively inventories, monitors and manages their corporate assets and digital footprint. An ad-hoc approach simply no longer works to manage external attack surfaces. Manual processes and legacy tools make managing your attack surface complex and expensive, and results are flooded with false positives and human errors. The more an organization grows the larger the attack surface becomes, increasing your risk exposure.
Edgescan’s external Attack Surface Management (ASM) is our most advanced solution yet, designed to detect threats across external services and bring unknowns into the platform for investigation by the security team. It solves the lack of visibility and remediation velocity that occurs with legacy tools and manual processes, making it the cornerstone of any modern-day continuous threat exposure management (CTEM) program.
Leverage cyber analytics and human expertise
Edgescan ASM uncovers attack vectors (two examples: ransomware and phishing) that can be used to breach your most critical assets, including data exposures and misconfigurations. The platform leverages both vulnerability data and business context to prioritize risk.
According to Gartner®...
“By 2026, organizations prioritizing their security investments, based on a continuous threat exposure management program, will realize a two-third reduction in breaches.”
Reduction
in breaches
Benefits of using Attack Surface Management
Complete visibility
The platform intelligently probes and identifies all networking devices, internet-facing devices, platforms, operating systems, databases, and web applications. It finds unknown assets across the entire internet, identifies security blind spots from discovered assets, discovers APIs, enumerates shadow IT and automates the analysis of changes across the entire IT ecosystem.
Map and inventory DNS/internet records
Discover existing records related to your deployed systems, servers, websites, APIs and applications.
Find and inventory related subdomains or obfuscated records that may direct an attacker to your internet footprint.
Unlimited and on-demand investigations
Run proactive and continuous investigations at the pace your organization requires.
The platform also provides complete flexibility to modify their deployment models whenever needed.
Get alerts for discoveries and exposures
Set up custom alerts and get notified of discoveries, then track and inventory exposures. Receive notifications when new systems are deployed, decommissioned or a system changes.
Edgescan Attack Surface Management (ASM) is a software as a service, sold as an annual subscription.
Contact us for more information on how Edgescan can help secure your business.
See How We Do Risk Management
Edgescan Attack Surface Management’s core purpose is to discover unknown domains, subdomains, related domains, and APIs, identifying security weaknesses such as misconfigurations, software vulnerabilities, exposed credentials and shadow IT that can be exploited by malign actors.
IT MANAGER
IT SECURITY MANAGER
NETWORK ADMINISTRATOR
CYBERSECURITY ANALYST
IT MANAGER
SECURITY OPERATIONS LEAD
CHIEF INFORMATION SECURITY OFFICER